In today’s fast-paced, data-driven world, colocation facilities have become an essential part of business infrastructure. These facilities provide a secure environment for businesses to house their IT systems, including servers, networking equipment, and storage solutions. With the growth of cloud computing and virtualization, the need for secure and efficient management of IT resources has only increased. Colocation facilities give organizations the ability to manage their own hardware in a highly controlled, reliable, and scalable environment, while also benefiting from shared resources like power, cooling, and internet connectivity.
However, the challenge of maintaining the security, reliability, and proper functioning of these facilities grows as more users and systems are involved. Given that colocation facilities host multiple clients’ sensitive data and physical infrastructure, controlling access to these environments is crucial. In order to maintain the security of the data center, strict access controls are required. This is where access lists come into play.
Access lists are crucial for defining who has permission to enter specific areas, which equipment they can interact with, and what actions they are authorized to take. This system helps the facility manage its personnel, monitor operations, and ensure that all users’ access is tracked and controlled in a highly secure manner.
In this blog post, we will explore in greater detail why access lists are necessary in a colocation facility, how they are implemented, and the different categories of users who rely on them: administrative users, technical users, and visitors. We will also discuss how these access lists are generally managed, typically through an online portal or via email, with recorded approval and oversight from the security team.
Why Access Lists Are Necessary in a Colocation Facility
Access lists are an indispensable tool in managing security and operational integrity within a colocation facility. The very nature of a colocation data center means that numerous businesses share the same physical space, yet they need to maintain complete control over their own equipment. This makes it essential to carefully define who has access to what, and why.
The key reasons why access lists are necessary in a colocation facility include:
-
Security: Security is the top priority in any data center, especially in a shared environment. Unauthorized access to sensitive equipment, whether intentional or accidental, can result in data breaches, hardware tampering, or even theft. Access lists ensure that only authorized personnel can enter secure areas and handle equipment. Additionally, access to certain areas is often restricted to specific times, preventing unauthorized individuals from wandering into areas where they shouldn’t be.
-
Accountability: Every action taken within a data center needs to be traceable. Access lists are integral in providing accountability for who enters the facility and what actions they perform. By maintaining an up-to-date list of all personnel with access rights, the facility can log and track any changes, movements, or activities within the building. This auditing process is vital for detecting anomalies, investigating incidents, and ensuring compliance with industry regulations.
-
Operational Efficiency: With many different types of users needing access to specific areas, access lists help streamline operations. Access rights are assigned based on roles, so that only those who need to perform specific tasks—whether it be maintenance, troubleshooting, or monitoring—are given access to the appropriate equipment or zones. This not only improves the overall flow of operations but also ensures that space and resources within the data center are optimally used.
-
Compliance: Many industries have strict compliance regulations when it comes to managing sensitive data and IT infrastructure. For example, regulations like HIPAA, GDPR, and PCI-DSS require businesses to demonstrate that they have proper access controls in place. Access lists play a vital role in ensuring that only the right people have access to sensitive data or hardware, and that all access is logged, monitored, and appropriately authorized. This is crucial when organizations need to provide evidence of their compliance efforts.
How Access Lists Work in a Colocation Facility
The way access lists are implemented varies depending on the specific facility and the tools available. However, the general concept remains the same: a system that grants specific access rights to different users based on their roles. The access rights typically define the zones they can enter, the times they are allowed access, and what actions they are authorized to perform.
Access Control Systems:
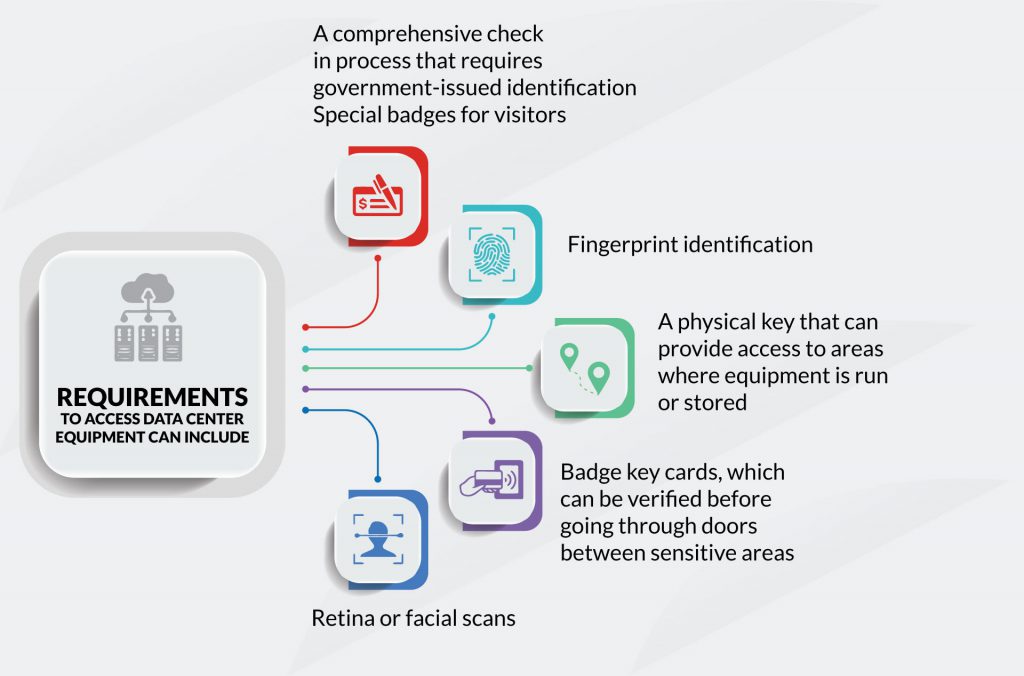
Most modern colocation facilities use electronic access control systems that manage entry and monitor activities. These systems include keycards, biometric scans (such as fingerprints or retina scans), PIN codes, or even mobile-based access credentials. These systems work by integrating with building management software that allows administrators to define specific access rights for each user.
Online Portal Management:
In many cases, access lists are maintained and updated through an online portal that allows administrators to easily add, remove, or adjust access rights for different users. These portals often provide real-time visibility into who has access to various areas of the data center and when. They also provide an easy way for users to request access and for administrators to approve or deny those requests.
For instance, an administrator may log into the portal, review a technician’s request for access, and grant access to a specific cabinet for a defined time. The system will automatically send a notification to the security team, which will approve or reject the access based on security protocols.
Email Approvals and Coordination:
In some cases, especially when access needs to be granted on a short-term or ad-hoc basis, access requests may be handled via email. An individual requesting access will send an email to the security team or data center administrator, providing their details, the area they need access to, and the purpose of their visit. The security team will review the request, ensure that it complies with access policies, and send an approval or denial email back to the requester.
This method is more manual than using a dedicated portal, but it is still commonly employed in smaller facilities or when an urgent request needs to be processed quickly.
Types of Access List Users
Access lists in a colocation facility are typically organized according to the types of users who require access. Each user type has distinct needs, and their access levels are granted accordingly. There are three main categories of access list users: administrative users, technical users, and visitors.
Administrative Users
Administrative users are typically the most powerful users in the data center. These are the account owners or managers who have the ability to control access for all other users. They are responsible for maintaining the integrity and security of the facility’s operations and have full control over the access list.
Key responsibilities of administrative users include:
- Managing and Updating Access Lists: Administrators can add or remove users, change access rights, and ensure the access policies align with business needs. They may create sub-users for different teams and assign appropriate roles and permissions.
- Setting Access Policies: Administrators define policies that determine who can access certain areas and when. For example, a policy may stipulate that only certain engineers can access high-security server rooms, or that visitors can only enter the lobby.
- Security and Compliance Oversight: Administrators track access logs and ensure that the facility is compliant with security and regulatory requirements. They may generate reports for auditing purposes and respond to incidents as they arise.
Technical Users
Technical users are typically members of the IT team, including technicians, engineers, and system administrators. These individuals need physical access to hardware and equipment in the data center, such as servers, storage units, or network switches.
Key responsibilities of technical users include:
- Hardware Maintenance and Upgrades: Technical users perform tasks like installing new hardware, replacing faulty components, or troubleshooting equipment. Their access is typically limited to specific cabinets or areas containing their equipment.
- Time-Limited Access: Technical users often require access during scheduled maintenance windows, and their access is carefully timed to avoid disruptions during peak business hours.
- Restricted Areas: While technical users have access to certain equipment, they typically do not have the ability to modify access policies or make changes to the broader facility’s security settings.
Visitor Users
Visitor access is granted to non-technical individuals who require temporary access to the facility, such as clients, vendors, contractors, or guests. Visitors typically do not need to interact with the equipment but may need to access common areas, meeting rooms, or other designated spaces.
Key responsibilities of visitor users include:
- Temporary Access: Visitors are often granted time-limited access based on their specific needs. For example, a vendor may need access for a few hours to install new equipment, while a guest might need access to attend a meeting or tour the facility.
- Limited Areas: Visitors are generally only allowed in specific areas such as conference rooms or lobbies, and are escorted by authorized personnel when necessary.
- Special Permissions: In some cases, visitors may be granted special permissions to access certain areas, such as a client requesting to view their own equipment or participate in a demonstration.
It comes down to integrity and security
Access lists are a critical element of managing security, accountability, and operational efficiency in colocation facilities. They ensure that only authorized individuals can access sensitive areas and equipment, while also providing a detailed record of who enters the facility and when. Whether an individual is an administrative user, a technical user, or a visitor, access lists help maintain the security of the data center while ensuring that only those who need access are granted it.
In many colocation facilities, access lists are managed through an online portal or via email, where requests are recorded and processed by the security team. This level of oversight helps maintain a high standard of security and ensures that only authorized individuals are allowed to interact with the data center’s infrastructure.
With proper access control measures in place, colocation facilities can ensure that their operations run smoothly and securely, providing a safe environment for both clients and their sensitive equipment. Whether you are an administrator, a technician, or a visitor, understanding and adhering to access policies is key to maintaining the integrity and security of the data center environment.
For Metanet, security is a very serious issue. We follow our access policy strictly. One example is if a billing representative of a company sends our support team an email with a domain name that does not match their company corporate domain (or one of their domain email accounts) sends a message to our support team asking for access to a bill, we would notify the admin of the account and request permission for the foreign requester to be permitted to be added to an access list so they can see internal corporate documentation and billing from their company account. Our customer portal makes available permissions for admin users to instantly choose their contacts for data center access, offering the choice or administrative, visitor temporary, or technical roles. This provides a convenient way to manage accounts and can also be used to prevent unauthorized access to the data center by an ex-employee or to provide granular access to third parties.